Intrusion Prevention System (IDS/IPS)¶
Zentyal integrates Suricata [2], one of the most popular IDS/IPS available for both Windows and Linux systems, as the IDS/IPS solution.
| [2] | Suricata: http://suricata-ids.org |
Configuring an IDS/IPS with Zentyal¶
Configuration of the IDS/IPS System in Zentyal is very easy. First, you have to specify on which network interfaces you need the IDS/IPS to listen to. After that, you can choose different groups of filters that will be applied to the captured traffic, in order to detect suspicious activity.
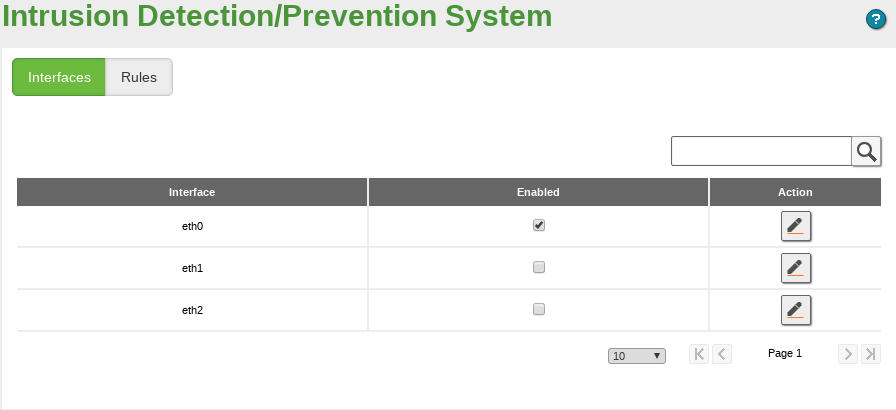
You can find both configuration options through the menu. In this section, on the Interfaces tab, a table with all the configured network interfaces will appear. All of them are disabled by default due to the increased network latency and CPU consumption caused by the traffic inspection. However, you can enable any of them by clicking on the checkbox.
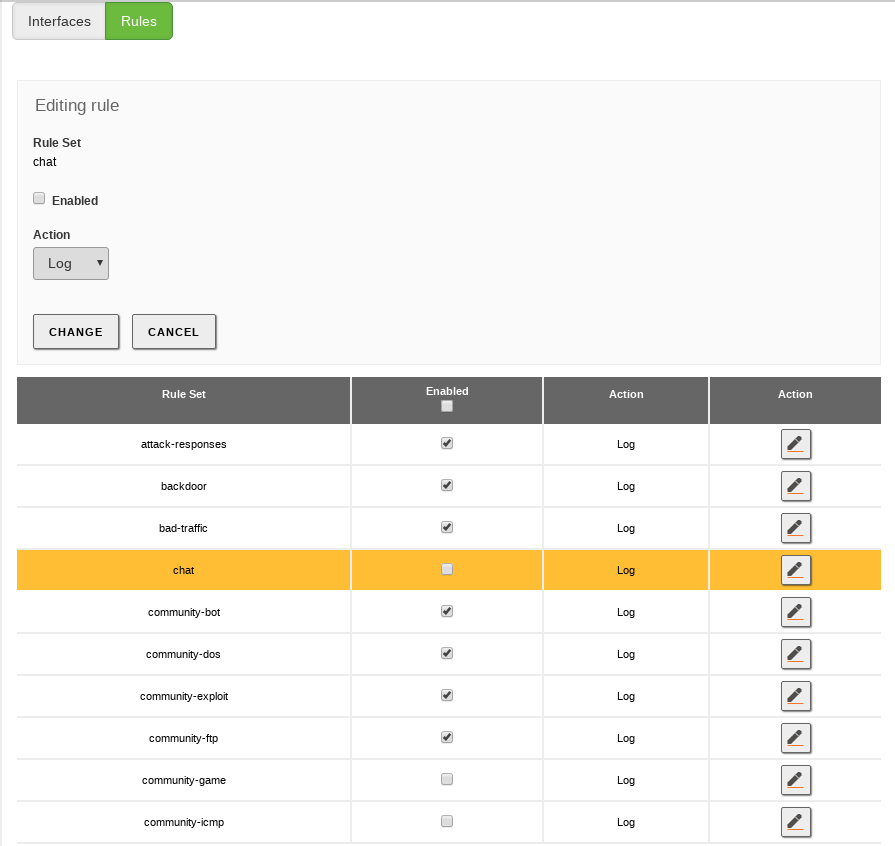
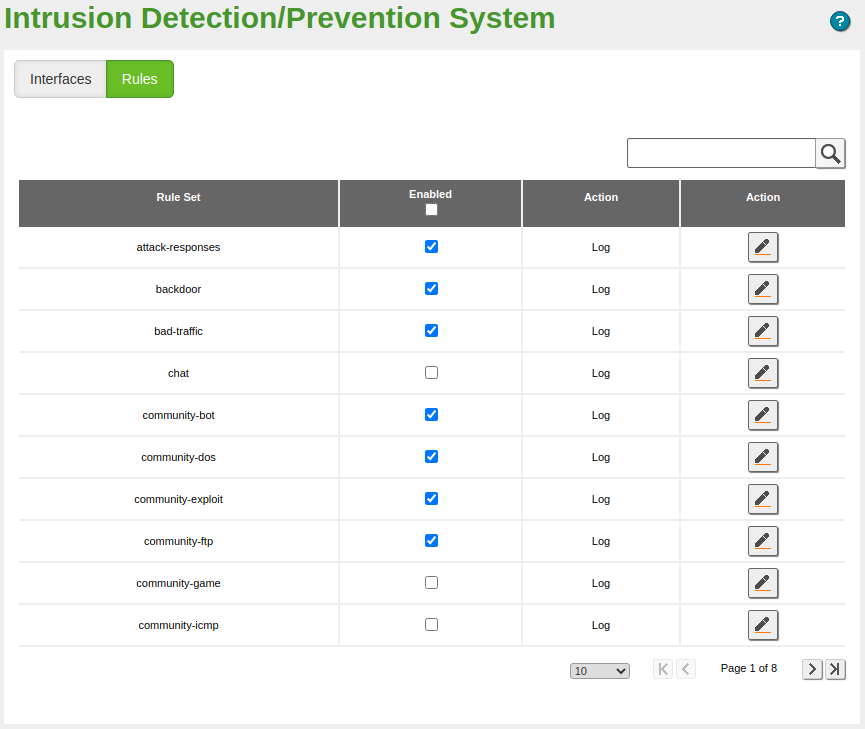
In the Rules tab, you have a preloaded table with all the Snort rulesets installed on your system. A typical set of rules is enabled by default. From this interface you can choose if you want to just Log (Default behaviour) or Block the source of the suspicious traffic.
You can save CPU time disabling those rules you are not interested in, for example, those related to services that are not available in your network. If you have extra hardware resources, you can also enable additional rules. The process of activating or deactivating a rule is the same as for Interfaces.