Zentyal as an Additional Domain Controller¶
In this entry we are going to explain how to join a Zentyal as an Additional Domain Controller to an existing domain controller managed by another Zentyal.
Table of Contents
Lab environment¶
The lab we have created to explain the process is:
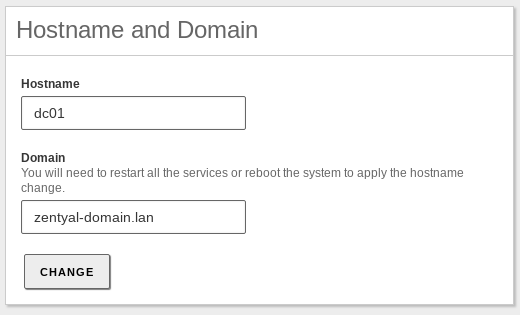
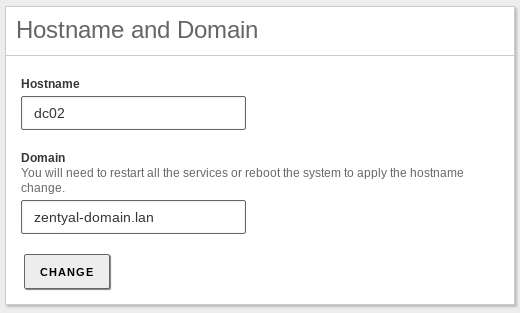
- Domain → zentyal-domain.lan
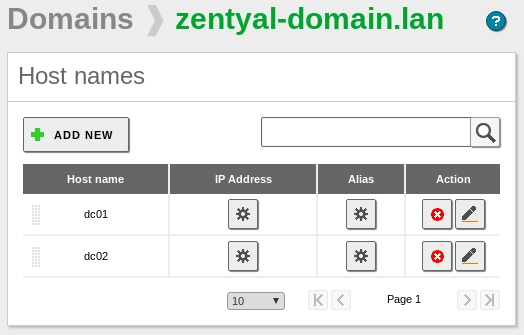
- First Domain Controller → dc01
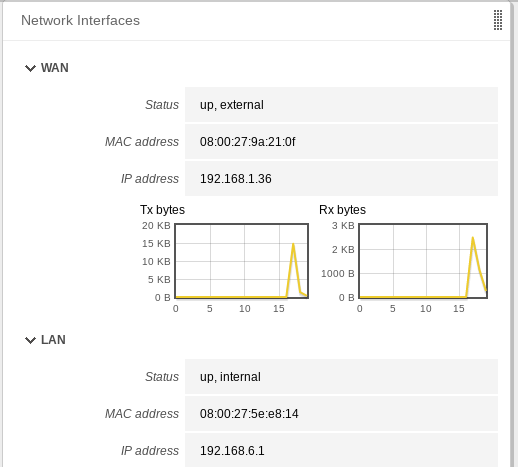
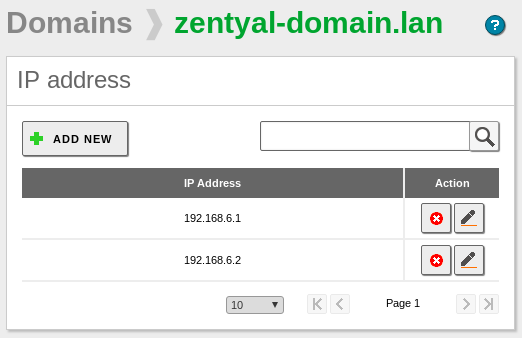
- First Domain Controller IP → 192.168.6.1
- Additional Domain Controller → dc02
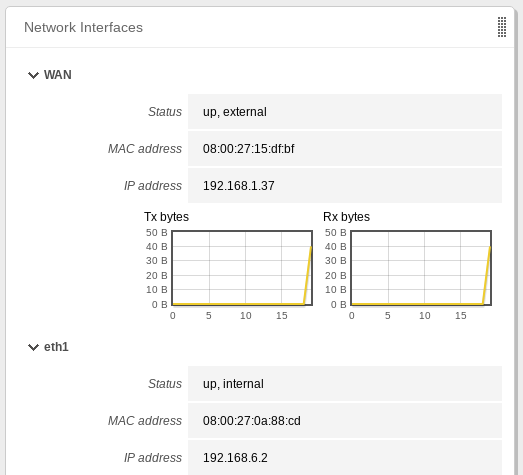
- Additional Domain Controller IP → 192.168.6.2
- Domain Admin user → admindc
Previous configuration¶
Firstly, you need to check the following tasks in both servers:
- The time must be properly configured.
- There are not important updates pending.
- The domain name must be the same on both Zentyal servers.
- Both Zentyal servers must be in the same network and they need to be reachable.
- None of the network adapters can be set up as ‘DHCP’.
Firewall configuration¶
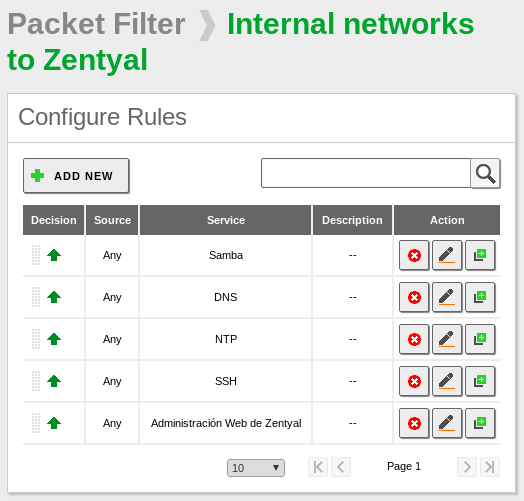
In order to allow the replication between the Zentyal servers you need to add a few rules in the correct section, in our case, the section is Internal networks to Zentyal:
NTP configuration¶
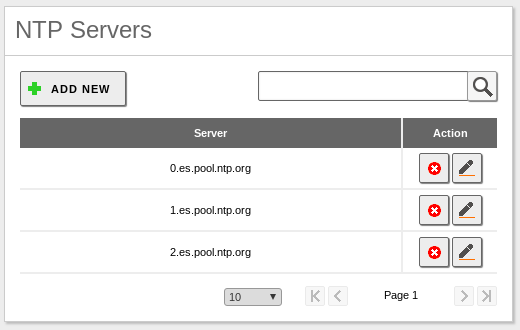
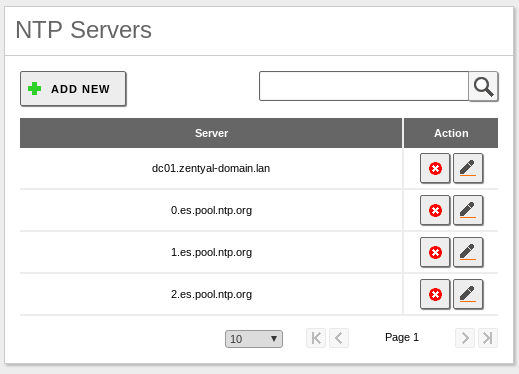
It’s a common practice to use the same official NTP server in both Zentyal servers to avoid issues with time:
From DC02 server:
DNS configuration¶
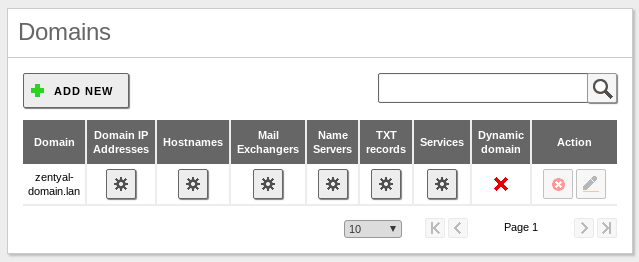
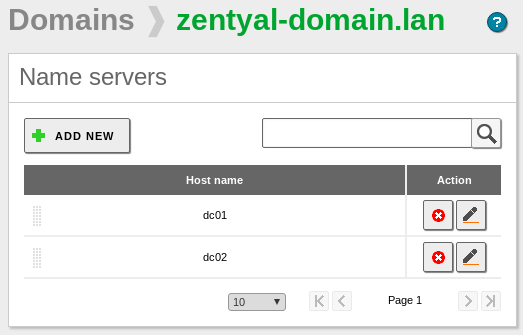
There a few records that should be present in both Zentyal servers in order to avoid issues during the replication events.
The name of the domain:
A records for the domain:
A records for the Zentyal servers:
A record for the DC01 server:
A record for the DC02 server:
NS records for the domain:
Checks before joining¶
Before continue with the configuration of the Zentyal DC02 server, we need to be sure that the Zentyal DC01 is estable.
Internal database of Samba¶
Ensure that you don’t have any critical errors in the internal database of Samba:
samba-tool dbcheck --cross-ncs
An example of its output:
Checking 3500 objects
Checked 3500 objects (0 errors)
In case of errors, you can run the following command to fix them:
samba-tool dbcheck --cross-ncs --fix --yes
Special DNS user¶
Check if the special DNS user belongs to the domain group DnsAdmins:
samba-tool group listmembers DnsAdmins 2> /dev/null
An example of its output:
dns-dc01
DNS CNAME record¶
Confirm that you have a DNS alias for the subdomain msdcs which points to the objectGUID of the DC01.
To get the ObjectGUID:
ldbsearch -H /var/lib/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | egrep "(dn|objectGUID):"
An example of its output:
dn: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=zentyal-domain,DC=lan
objectGUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
To make a DNS query that will tell us if the record exits:
host -t CNAME 9ffac3f8-4047-412e-bcef-39dcec51f187._msdcs.zentyal-domain.lan
An example of its output:
9ffac3f8-4047-412e-bcef-39dcec51f187._msdcs.zentyal-domain.lan is an alias for dc01.zentyal-domain.lan.
In case we don’t have this record, you will need to create it using ‘samba-tool dns’ command, an example below:
samba-tool dns add 127.0.0.1 _msdcs.zentyal-domain.lan 9ffac3f8-4047-412e-bcef-39dcec51f187 CNAME dc01.zentyal-domain.lan -U admindc
Warning
Admindc is an user who has Domain Admins privileges, replace it for yours.
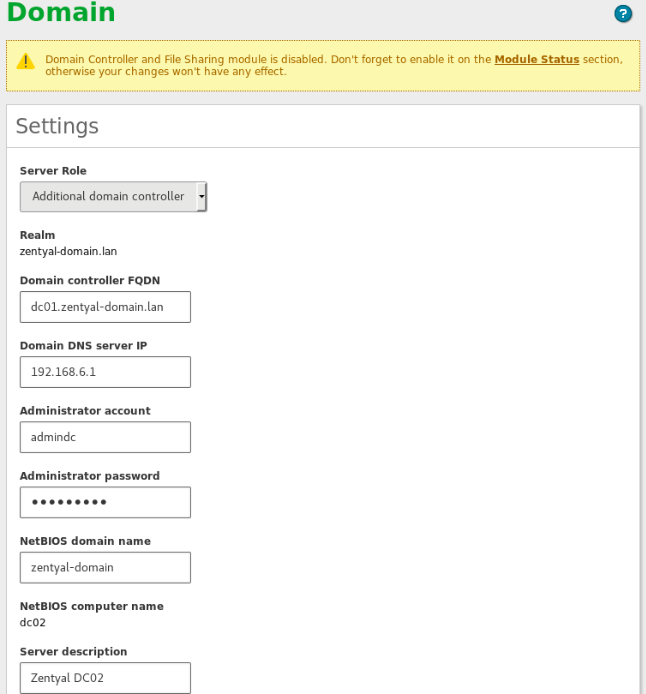
ADC configuration¶
Once you did all the above steps, you need to configure the Zentyal DC02 server as an Additional Domain Controller:
Before enable the module, you need to check if both Zentyal servers have connectivity between them.
From DC01:
ping -c2 dc02.zentyal-domain.lan
An example of its output:
PING dc02.zentyal-domain.lan (192.168.6.2) 56(84) bytes of data.
64 bytes from dc02.zentyal-domain.lan (192.168.6.2): icmp_seq=1 ttl=64 time=0.534 ms
64 bytes from dc02.zentyal-domain.lan (192.168.6.2): icmp_seq=2 ttl=64 time=0.434 ms
--- dc02.zentyal-domain.lan ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.434/0.484/0.534/0.050 ms
From DC02:
ping -c2 dc01.zentyal-domain.lan
An example of its output:
PING dc01.zentyal-domain.lan (192.168.6.1) 56(84) bytes of data.
64 bytes from dc01.zentyal-domain.lan (192.168.6.1): icmp_seq=1 ttl=64 time=0.444 ms
64 bytes from dc01.zentyal-domain.lan (192.168.6.1): icmp_seq=2 ttl=64 time=0.534 ms
--- dc01.zentyal-domain.lan ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.444/0.489/0.534/0.045 ms
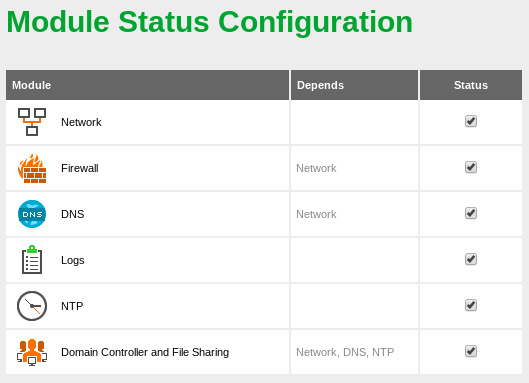
Once we have confirmed the connectivity, we can proceed to enable the Domain Controller module in order to join this DC02 server to the domain:
If everything was fine, in the log file /var/log/zentyal/zentyal.log you will see the following records:
From DC01:
2020/05/06 11:13:18 INFO> SyncDaemon.pm:125 EBox::Samba::SyncDaemon::checkUsers - Set user 'CN=dns-DC02,CN=Users,DC=zentyal-domain,DC=lan' uidNumber=65539
2020/05/06 11:13:18 INFO> SyncDaemon.pm:131 EBox::Samba::SyncDaemon::checkUsers - Set user 'CN=dns-DC02,CN=Users,DC=zentyal-domain,DC=lan' gidNumber=2513
2020/05/06 11:13:19 INFO> SyncDaemon.pm:147 EBox::Samba::SyncDaemon::checkUsers - Set user 'CN=dns-DC02,CN=Users,DC=zentyal-domain,DC=lan' homeDrive='H:' homeDirectory='\\dc01.ZENTYAL-DOMAIN.LAN'
From DC02:
2020/05/06 11:12:00 INFO> Samba.pm:388 EBox::Samba::setupDNS - Setting up DNS
2020/05/06 11:12:20 INFO> GlobalImpl.pm:616 EBox::GlobalImpl::saveAllModules - Saving config and restarting services: firewall dns samba logs
2020/05/06 11:12:20 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: firewall
2020/05/06 11:12:21 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: dns
2020/05/06 11:12:33 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: samba
2020/05/06 11:12:38 INFO> Provision.pm:810 EBox::Samba::Provision::checkAddress - Resolving dc01.zentyal-domain.lan to an IP address
2020/05/06 11:12:38 INFO> Provision.pm:830 EBox::Samba::Provision::checkAddress - The DC dc01.zentyal-domain.lan has been resolved to 192.168.6.1
2020/05/06 11:12:38 INFO> Provision.pm:833 EBox::Samba::Provision::checkAddress - Checking reverse DNS resolution of '192.168.6.1'...
2020/05/06 11:12:38 INFO> Provision.pm:854 EBox::Samba::Provision::checkAddress - The IP address 192.168.6.1 has been resolved to dc01.zentyal-domain.lan
2020/05/06 11:12:38 INFO> Provision.pm:756 EBox::Samba::Provision::checkServerReachable - Checking if AD server '192.168.6.1' is online...
2020/05/06 11:12:38 INFO> Provision.pm:866 EBox::Samba::Provision::checkFunctionalLevels - Checking forest and domain functional levels...
2020/05/06 11:12:39 INFO> Provision.pm:898 EBox::Samba::Provision::checkRfc2307 - Checking RFC2307 compliant schema...
2020/05/06 11:12:40 INFO> Provision.pm:775 EBox::Samba::Provision::checkLocalRealmAndDomain - Checking local domain and realm...
2020/05/06 11:12:41 INFO> Provision.pm:972 EBox::Samba::Provision::checkClockSkew - Checking clock skew with AD server...
2020/05/06 11:12:41 INFO> Provision.pm:993 EBox::Samba::Provision::checkClockSkew - Clock skew below two minutes, should be enough.
2020/05/06 11:12:41 INFO> Provision.pm:675 EBox::Samba::Provision::checkDnsZonesInMainPartition - Checking for old DNS zones stored in main domain partition...
2020/05/06 11:12:42 INFO> Provision.pm:722 EBox::Samba::Provision::checkForestDomains - Checking number of domains inside forest...
2020/05/06 11:12:42 INFO> Provision.pm:932 EBox::Samba::Provision::checkTrustDomainObjects - Checking for domain trust relationships...
2020/05/06 11:12:44 INFO> Provision.pm:1034 EBox::Samba::Provision::checkADServerSite - Checking the site where the specified server is located
2020/05/06 11:12:44 INFO> Provision.pm:1042 EBox::Samba::Provision::checkADServerSite - The specified server has been located at site named Default-First-Site-Name
2020/05/06 11:12:44 INFO> Provision.pm:1059 EBox::Samba::Provision::checkADNebiosName - Checking domain netbios name...
2020/05/06 11:12:47 INFO> Provision.pm:1286 EBox::Samba::Provision::provisionADC - Joining to domain 'zentyal-domain.lan' as DC
2020/05/06 11:12:49 INFO> Provision.pm:1299 EBox::Samba::Provision::provisionADC - Trying to get a kerberos ticket for principal 'admindc@ZENTYAL-DOMAIN.LAN'
2020/05/06 11:12:49 INFO> Provision.pm:1308 EBox::Samba::Provision::provisionADC - Executing domain join
2020/05/06 11:13:20 INFO> Provision.pm:299 EBox::Samba::Provision::setupKerberos - Setting up kerberos
2020/05/06 11:13:20 INFO> Provision.pm:276 EBox::Samba::Provision::setupDNS - Setting up DNS
2020/05/06 11:13:21 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: dns
2020/05/06 11:14:47 WARN> Samba.pm:561 EBox::Samba::_waitService - Timeout reached while waiting for users service 'Lightweight Directory Access Protocol' (tcp)
2020/05/06 11:15:01 INFO> Provision.pm:1089 EBox::Samba::Provision::_addForestDnsZonesReplica - Adding Forest Dns replica
2020/05/06 11:15:06 INFO> Provision.pm:1120 EBox::Samba::Provision::_addDomainDnsZonesReplica - Adding Domain Dns replica
2020/05/06 11:15:06 INFO> Provision.pm:1336 EBox::Samba::Provision::provisionADC - Waiting RID pool allocation
2020/05/06 11:15:07 INFO> Provision.pm:1340 EBox::Samba::Provision::provisionADC - Running KCC on remote DC
2020/05/06 11:15:42 INFO> SyncDaemon.pm:340 EBox::Samba::SyncDaemon::run - Samba sync daemon started
2020/05/06 11:16:12 INFO> Samba.pm:776 EBox::Samba::_postServiceHook - Writing DNS update list...
2020/05/06 11:16:21 INFO> LDAP.pm:246 EBox::Module::LDAP::_sendSchemaUpdate - Sending schema update:
2020/05/06 11:16:22 INFO> LDAP.pm:246 EBox::Module::LDAP::_sendSchemaUpdate - Sending schema update:
2020/05/06 11:16:23 INFO> LDAP.pm:304 EBox::Module::LDAP::waitForLDAPObject - Waiting for schema object present: CN=quota,CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
2020/05/06 11:16:23 INFO> LDAP.pm:304 EBox::Module::LDAP::waitForLDAPObject - Waiting for schema object present: CN=systemQuotas,CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
2020/05/06 11:16:30 INFO> SyncDaemon.pm:340 EBox::Samba::SyncDaemon::run - Samba sync daemon started
2020/05/06 11:16:34 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: logs
2020/05/06 11:16:38 INFO> Base.pm:231 EBox::Module::Base::save - Restarting service for module: dns
2020/05/06 11:19:24 INFO> GlobalImpl.pm:714 EBox::GlobalImpl::saveAllModules - Changes saved successfully
A common error when enabling the module¶
It is normal to get an error when you saving the changes related to the DNS module, this is because sometimes Samba doesn’t add the special DNS user to the domain group ‘DnsAdmins’ when the join is made, however, besides this error the objects should be replicated.
To confirm the issue, you will have an error like this in the log file /var/log/zentyal/zentyal.log:
2020/05/06 11:17:24 ERROR> Sudo.pm:240 EBox::Sudo::_rootError - root command nsupdate -g -t 10 /var/lib/zentyal/tmp/oljKMX0500 failed.
Error output: update failed: REFUSED
To fix it, in the DC01 you have to add the new special DNS user to the DnsAdmins users:
samba-tool group addmembers DnsAdmins dns-dc02
Then, in the dc02 server we need to restart two modules:
zs dns restart
zs samba restart
Test after joining¶
Once the Zentyal DC02 server is joined as Domain Controller , there are a few tests that must be done in order to confirm the stability of the deploy.
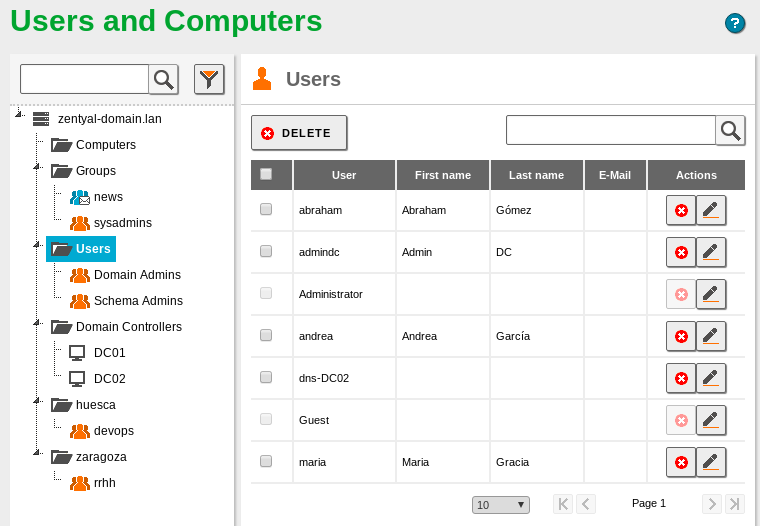
Objects replicated¶
The first test should be check in the Webadmin of both Zentyal servers that all the objects were replicated correctly:
Special DNS user¶
Ensure that both special DNS users belong to the domain group DnsAdmins by running the following command in both Zentyal servers:
samba-tool group listmembers DnsAdmins 2> /dev/null
An example of its output:
dns-dc01
dns-DC02
CNAME record¶
Obtain the objectGUID of both domain controllers:
ldbsearch -H /var/lib/samba/private/sam.ldb '(invocationId=*)' --cross-ncs objectguid | egrep "(dn|objectGUID):"
An example of its output:
dn: CN=NTDS Settings,CN=DC02,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=zentyal-domain,DC=lan
objectGUID: 37fe3168-1c97-4286-b5d2-da79745484ad
dn: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=zentyal-domain,DC=lan
objectGUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Then, we need to make a DNS query in order to confirm that there is a CNAME record for each of Zentyal server:
host -t CNAME 9ffac3f8-4047-412e-bcef-39dcec51f187._msdcs.zentyal-domain.lan
host -t CNAME 37fe3168-1c97-4286-b5d2-da79745484ad._msdcs.zentyal-domain.lan
An example of its output:
9ffac3f8-4047-412e-bcef-39dcec51f187._msdcs.zentyal-domain.lan is an alias for dc01.zentyal-domain.lan.
37fe3168-1c97-4286-b5d2-da79745484ad._msdcs.zentyal-domain.lan is an alias for DC02.zentyal-domain.lan.
In case any DNS record is missing, we will need to add it using samba-tool dns command in the DC01 server, below there is an example:
samba-tool dns add 127.0.0.1 _msdcs.zentyal-domain.lan 37fe3168-1c97-4286-b5d2-da79745484ad CNAME dc02.zentyal-domain.lan -U admindc
Warning
Admindc is an user who has Domain Admins privileges, replace it for yours.
Once the CNAME record is added, we will need to restart the Domain Controller module in the server who doesn’t have the record:
zs samba restart
DC Subdomain¶
Another important check that we need to do is to confirm that the subdomain ‘msdcs.’ has a NS record for both Zentyal servers:
host -t NS _msdcs.zentyal-domain.lan
An example of its output:
_msdcs.zentyal-domain.lan name server dc01.zentyal-domain.lan.
_msdcs.zentyal-domain.lan name server dc02.zentyal-domain.lan.
In case a NS record is missing, we will need to create it through samba-tool dns command from DC01, below there an example:
samba-tool dns add 127.0.0.1 _msdcs.zentyal-domain.lan @ NS dc02.zentyal-domain.lan -U admindc
Warning
Admindc is an user who has Domain Admins privileges, replace it for yours.
Finally, confirm that the record was properly added and replicated between the Zentyal servers.
Replication status¶
Check the status of the replication by running the following command in both servers:
samba-tool drs showrepl 2> /dev/null
An example of its output from the DC01:
Default-First-Site-Name\DC01
DSA Options: 0x00000001
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
DSA invocationId: 2530ee47-6810-41cc-b956-3b93d29ce901
==== INBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ Wed May 6 11:52:19 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:52:19 2020 CEST
CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ Wed May 6 11:52:19 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:52:19 2020 CEST
DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ Wed May 6 11:52:19 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:52:19 2020 CEST
DC=DomainDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ Wed May 6 11:52:19 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:52:19 2020 CEST
DC=ForestDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ Wed May 6 11:52:19 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:52:19 2020 CEST
==== OUTBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC02 via RPC
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 5e6bb01d-3928-4921-bf60-fa2dc5b0a44b
Enabled : TRUE
Server DNS name : dc02.zentyal-domain.lan
Server DN name : CN=NTDS Settings,CN=DC02,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=zentyal-domain,DC=lan
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
An example of its output from the DC02:
Default-First-Site-Name\DC02
DSA Options: 0x00000001
DSA object GUID: 37fe3168-1c97-4286-b5d2-da79745484ad
DSA invocationId: d3477fdb-594a-42f2-9f87-d6ddbf2bd8c3
==== INBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ Wed May 6 11:56:14 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:56:14 2020 CEST
CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ Wed May 6 11:56:14 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:56:14 2020 CEST
DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ Wed May 6 11:56:14 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:56:14 2020 CEST
DC=DomainDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ Wed May 6 11:56:14 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:56:14 2020 CEST
DC=ForestDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ Wed May 6 11:56:14 2020 CEST was successful
0 consecutive failure(s).
Last success @ Wed May 6 11:56:14 2020 CEST
==== OUTBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=zentyal-domain,DC=lan
Default-First-Site-Name\DC01 via RPC
DSA object GUID: 9ffac3f8-4047-412e-bcef-39dcec51f187
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 778a738f-b5c1-44ff-8f1f-0a07e9070867
Enabled : TRUE
Server DNS name : dc01.zentyal-domain.lan
Server DN name : CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=zentyal-domain,DC=lan
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
Replication events¶
Create one test user or group and a DNS record for each Zentyal server in order to confirm that the replication is working fine. Below we can see an example of the records that we get in the log file /var/log/samba/samba.log related to an object replication:
From the server where the object was created:
[2020/05/06 12:05:16.933303, 2] ../source4/rpc_server/drsuapi/getncchanges.c:3006(dcesrv_drsuapi_DsGetNCChanges)
DsGetNCChanges with uSNChanged >= 3978 flags 0x80000074 on <GUID=4cc532cc-bcd3-4d5a-8333-3e5f7c9fff8e>;<SID=S-1-5-21-3072287442-1279753506-2244781692>;DC=zentyal-domain,DC=lan gave 1 objects (done 1/1) 0 links (done 0/0 (as S-1-5-21-3072287442-1279753506-2244781692-1112))
From the server where the object is replicated:
[2020/05/06 12:05:38.179657, 2] ../source4/dsdb/repl/replicated_objects.c:1020(dsdb_replicated_objects_commit)
Replicated 1 objects (0 linked attributes) for DC=zentyal-domain,DC=lan