VPN Service with IPsec and L2TP/IPSEC¶
Zentyal integrates Libreswan [3] as its IPsec and L2TP/IPsec solution. This service uses the ports 500, 1701 and 4500 of UDP and the ESP protocol.
| [3] | http://libreswan.org/ |
Configuring an IPsec tunnel in Zentyal¶
Before start with the configuration, note that this module is only available for Zentyal Commercial Edition.
To configure IPsec in Zentyal go to . Here you can define all the tunnels and IPsec connections you need. You can enable or disable each one of them and add an explanatory text.
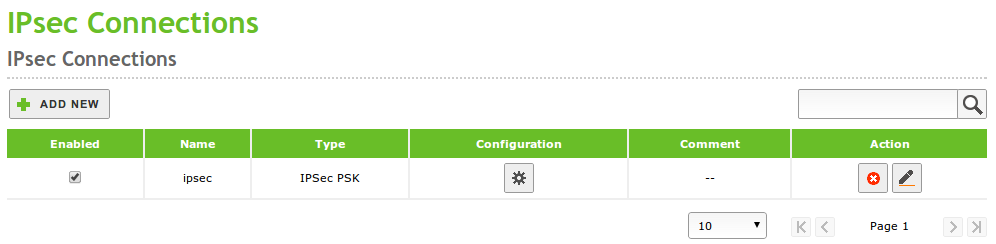
IPsec connections
Inside Configuration, and the General tab you will define the Zentyal’s IP address that you will use in each connection to access the external subnet, the local subnet behind Zentyal that will be accessible through the VPN tunnel, the remote IP address you will contact in the other end of the tunnel and the local subnetwork you will have available in the other end. If you want to configure a tunnel between two networks using IPsec, both ends must have a static IP address.
Currently Zentyal supports PSK authentication only (preshared key), which you can configure under PSK preshared key.
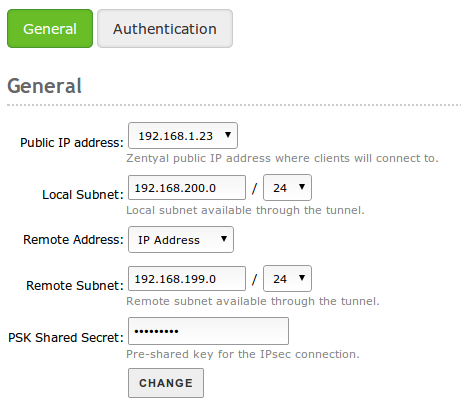
IPSEC General configuration
In the Authentication tab you will configure the specific parameters of the tunnel authentication. This parameters determine the behaviour of the IPsec protocol and have to be identical in both ends of the tunnel. To learn more about the meaning of each one of the options, check IPsec specific documentation.
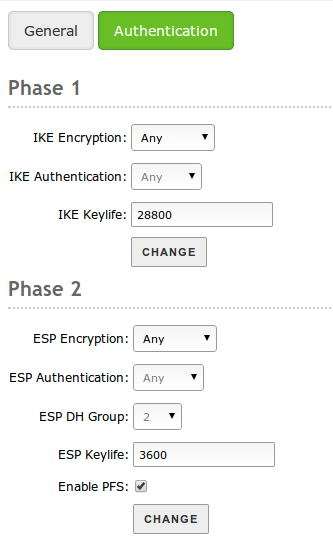
Authentication configuration
Configuring an L2TP/IPsec tunnel in Zentyal¶
To configure a L2TP-type tunnel the steps are similar, but going to , you will choose the type L2TP/IPSEC PSK.
The general configuration has some differences:
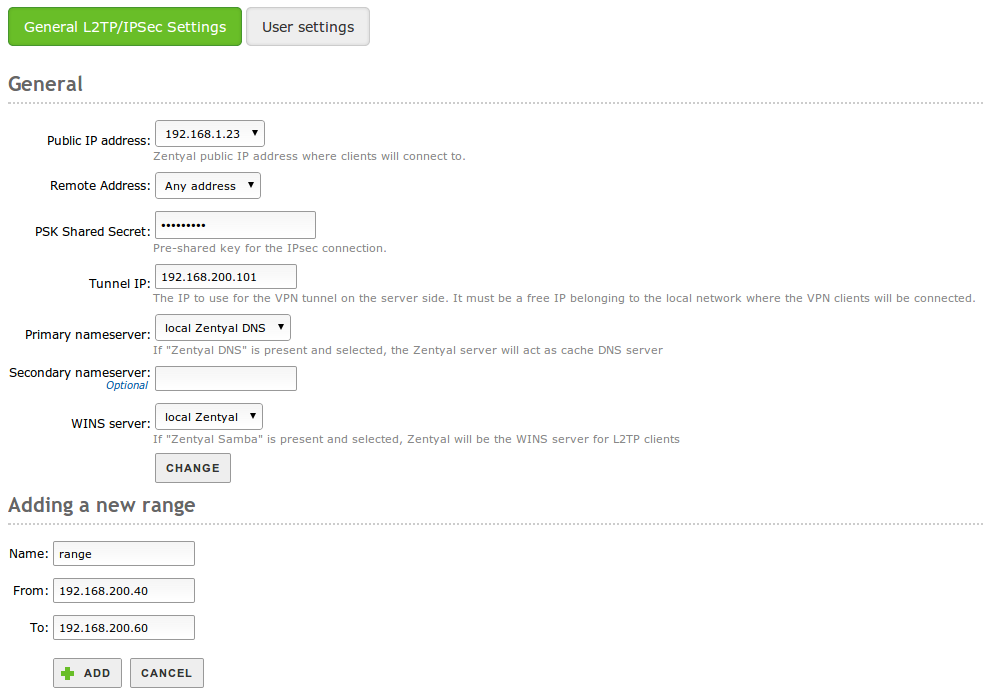
General L2TP/IPSEC Configuration
Instead of connecting subnets, like IPSEC default configuration, L2TP configures a LAC (L2TP Access Concentrator) with the IP specified in Tunnel IP, the users connected to this LAC will acquire a valid IP in the local network where the LAC is registered, thus being able to communicate with any other LAN client.
You can configure a range of IP addresses, in similar fashion to DHCP ranges, for the incoming L2TP/IPSEC VPN clients.
L2TP/IPSEC has two possible sources of users, a custom users list or a group of domain users.
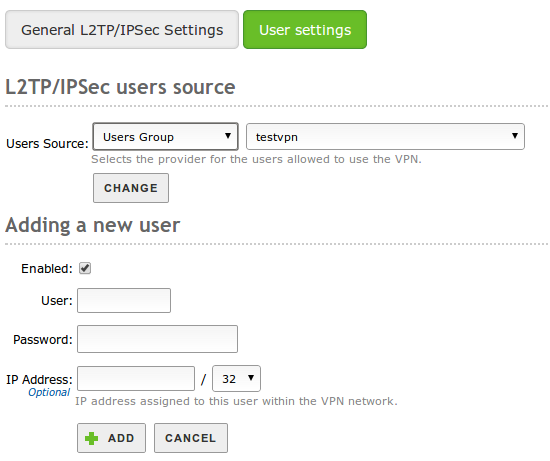
L2TP Users source
The two possible sources are mutually exclusive, Domain Controller and File Sharing are needed in order to have Users group as an option. If you choose the Manual list of users option, you can choose to assign the IP statically, while the Samba users group will make use of the IP ranges described above.