First steps with Zentyal¶
Zentyal webadmin interface¶
Once you have installed Zentyal, you can access Zentyal’s administrative web interface using its own graphical environment included in the installer, or from any point of the internal network, using the address: “https://ip_address:8443”, where ip_address is the IP address or the hostname on which Zentyal is installed. This web administration page is always accessed using HTTPS, so the first time, the browser will ask you whether you trust the site. You can safely accept the self-generated certificate.
Warning
Older versions of Internet Explorer may have problems accessing the interface. Use the last stable version of your web browser.
The login screen asks for the username and password. The user created during the installation and any other user of the sudo group can authenticate as a Zentyal administrator.
Once authenticated, you will see the administrative interface, this is divided in three main parts:
- Left side menu:
- Contains links to all the services that can be configured by using Zentyal, separated into categories. When you select a service in this menu, a sub menu might appear to configure a particular requirement in the selected service.
- Top menu:
- Contains actions:Logging out of the session and the ‘Save Changes’ button if needed.
- Main content:
- The content that occupies the central part, consists of one or more forms or tables with information about service configuration that are selected through the left side menu and its sub menus. Sometimes, in the top, you can see a menu with tabs or buttons: each tab represents a different subsection within the section you have accessed.
Dashboard¶
The Dashboard is the “home” interface. It contains a series of widgets that can be configured. You can reorganize the widgets at any time by clicking on their titles and dragging them.
By clicking on Configure Widgets a new menu appears, allowing you to remove and add new widgets. To add a new widget, you need to search for it using the top menu and drag it to the central section. To remove a widget, click on the X in the upper right corner of the window.
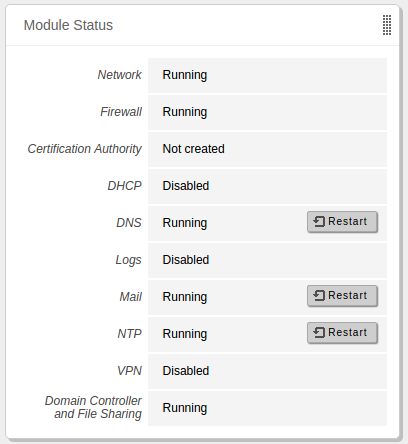
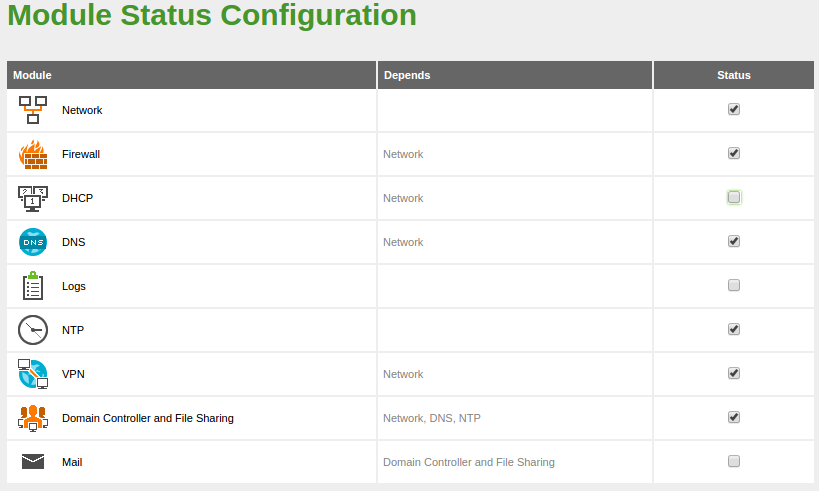
One of the most important widgets in the Dashboard displays the status of all modules installed on Zentyal.
The image shows the status of a service and the action you can carry out for this service. The different statuses are:
- Running:
- The service is running and listening to client connections. You can restart a service using Restart.
- Running unmanaged:
- If you haven’t enabled the module yet, it will be running with the default configuration set by the distribution.
- Stopped:
- The service is stopped either because the administrator has stopped it or because a problem has occurred. You can restart the service by clicking on Restart.
- Disabled:
- The module has been explicitly disabled by the administrator.
Configuration of the module status¶
Zentyal uses a modular design in which each module manages a different service. To configure each of these services you must enable the corresponding module from . All those functions that have been selected during the installation will be enabled automatically.
Each module may have dependencies on others modules in order to work. For instance, DHCP module needs to have the network module enabled so that it can serve IP addresses through the configured network interfaces. The dependencies are shown in the Depends column and until these are enabled, you can’t enable the module.
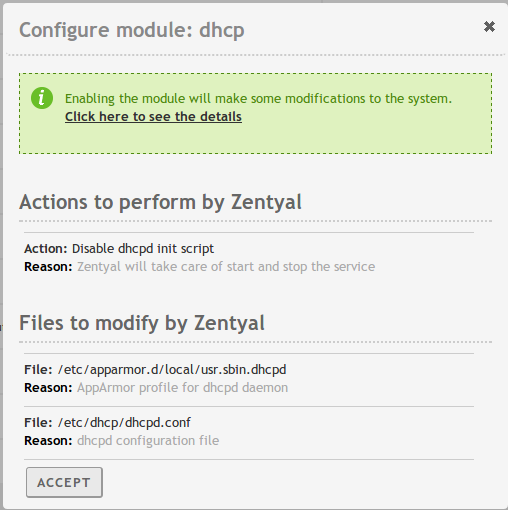
The first time you enable a module, you are asked to accept the set of actions that will be carried out and the configuration files that will be overwritten. After you have accepted all the actions and listed files, you must save changes in order to apply the configuration.
Warning
If you do manual modifications on any file managed by a module, for example /etc/dhcp/dhcpd.conf for the DHCP module, it will be overwritten next time you click Save Changes. If you need to do custom changes on the way that file is genearated, check Appendix A: Development and advanced configuration.
Applying the configuration changes¶
An important feature to consider when working with Zentyal is the way configuration changes are applied. First, changes must be accepted in the module forms. Then, to make these changes effective and apply them permanently you must click on the Save Changes button in the top menu. This button will only appear if there are any unsaved changes. By clicking on this button, you will see a confirmation dialogue where you can also discard unsaved changes. An exception to this rule is the users and groups management: here the changes are applied directly to the LDAP database.
Warning
If you change the network interface configurations, firewall or administrative interface port, you might loose the connection. If this is the case you should change the URL in the browser or reconfigure through the local GUI.
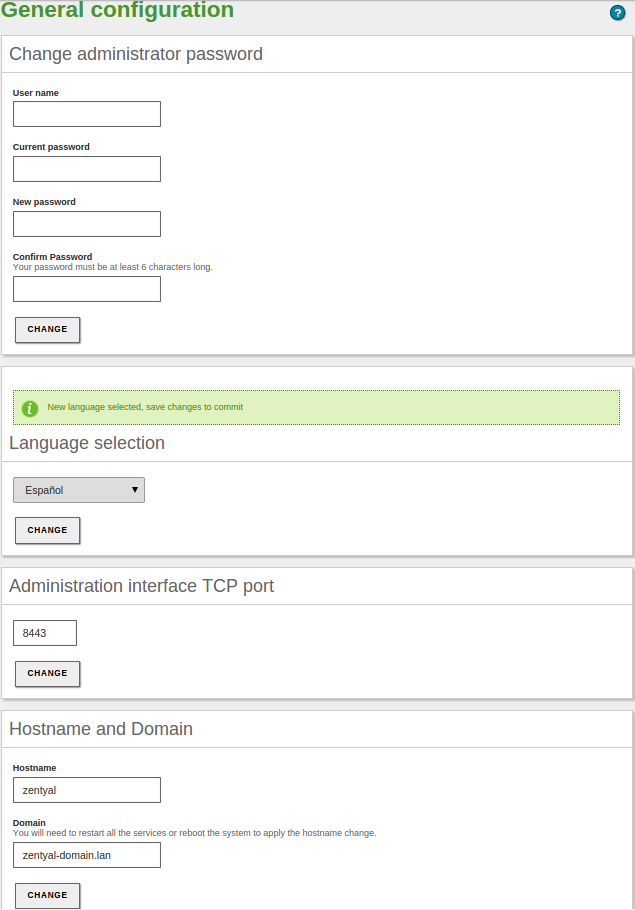
General configuration¶
There are several parameters in the general configuration of Zentyal that can be modified in .
- Password:
- You can change the password of an administrative user.
- Language:
- You can change the interface language using Select a language.
- Administrative interface port:
- By default, it is the HTTPS port 443, but if you want to use it for the web server, you must change it to another port and specify it in the URL when you access https://ip_address:port/.
- Hostname:
- It is possible to change the hostname or the domain, for example zentyal.home.lan. The hostname will be used as a A register (hostname) of the local DNS domain.
Warning
You have to be careful if you intend to change the machine host name or local domain after the installation, because the authentication subsystems (Kerberos) will be automatically reconfigured. It’s recommended to reboot the machine after this operation, so all the daemons are aware of the change.
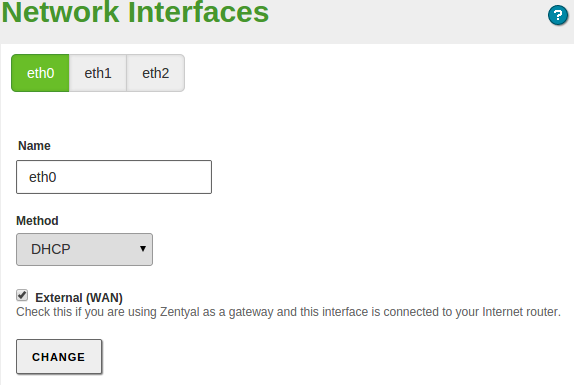
Network configuration with Zentyal¶
Through you can access the configuration of each network card detected by the system and you can select between a static configuration (manually configured), dynamic (DHCP configuration), VLAN (802.1Q) trunk, PPPoE or bridged.
In addition, you can define each interface to be External if it is connected to an external network, such as the Internet, in order to apply stricter firewall policies. If you don’t do this, the interface is considered internal, connected to a local network.
Warning
Zentyal will only grant Internet access to the clients in the local network if the ‘Firewall’ module is installed and enabled.
DHCP client interface¶
When you configure an interface to make DHCP requests, you are not configuring only the IP address, but also the DNS servers and gateway. This is usual for hosts within the local network or for external interfaces connected to the infrastructure routers.
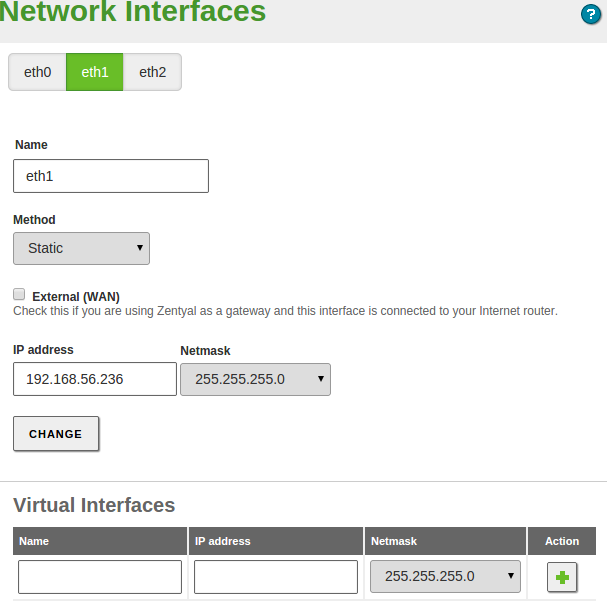
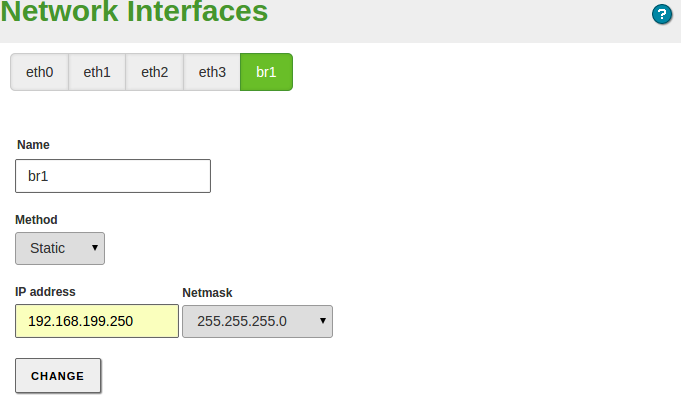
Static interface¶
If you decide to configure a static interface you must specify the IP address and the network mask. You can also associate one or more Virtual Interface to this real interface to use additional IP addresses.
These additional addresses are useful to provide a service in more than one IP address or sub-network, to facilitate the migration from a previous scenario or to have a web server with different domains using SSL certificates.
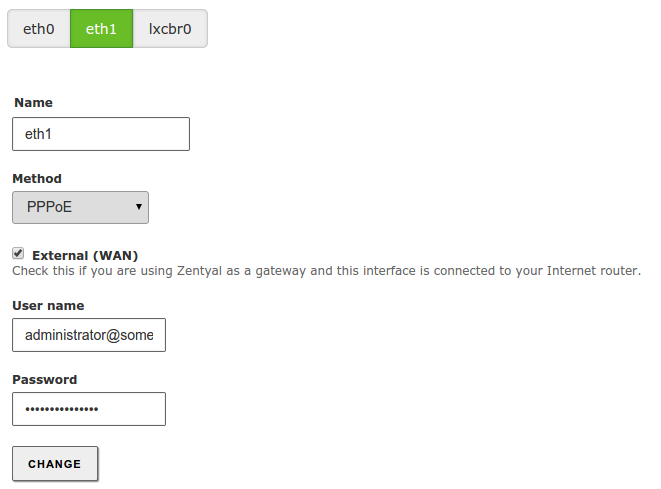
PPPoE¶
If you use an ADSL router PPPoE [1] (a connection method used by some Internet providers), you can also configure these types of connections. To do this, you only have to select PPPoE and introduce the Username and Password supplied by your provider.
| [1] | http://en.wikipedia.org/wiki/PPPoE |
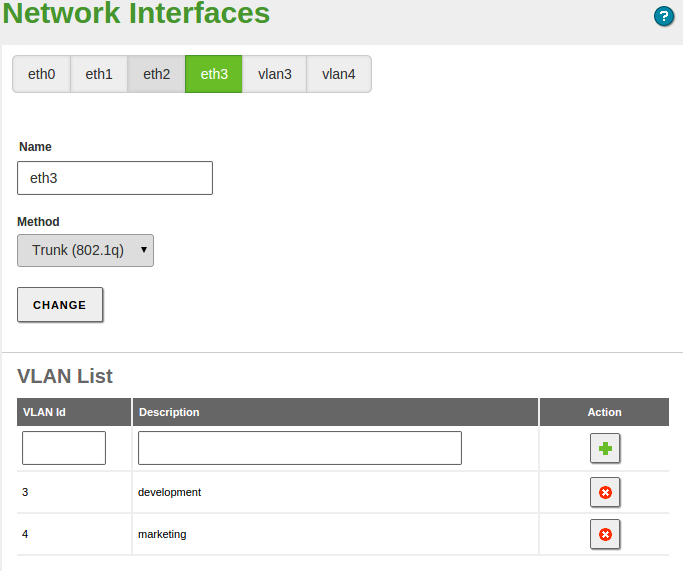
VLAN trunk¶
If you connect the server to one or more VLAN networks, select Trunk (802.11q). Once selected, using this method you can create as many interfaces associated to the defined tag as you wish, and consider them as if they were real interfaces.
The VLAN network infrastructure allows you to segment the local network to improve performance and security, without the need to invest in hardware that would usually be necessary to create each segment.
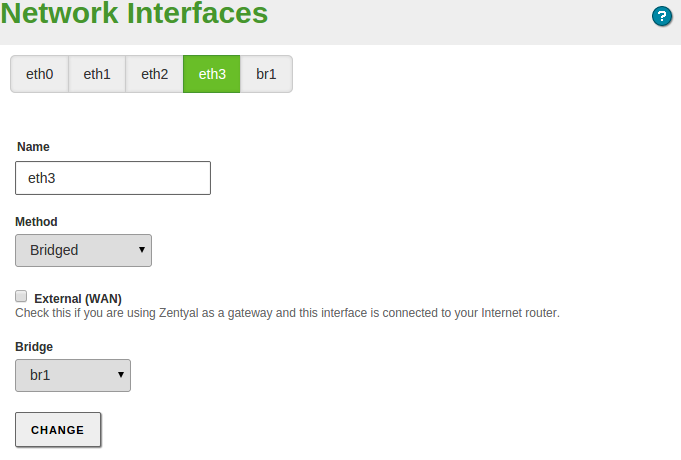
Bridged mode¶
The bridged mode consists of associating two physical network interfaces attached to your server that are connected to two different networks. For example, one card connected to the router and another card connected to the local network. By using this association you can redirect the network traffic transparently from one card to the other.
The main advantage here, is that client configurations do not need changing when the Zentyal server gateway is deployed. Traffic that passes through the server can be managed using content filtering or the intrusion detection system.
You can create this association by changing the interface with Bridged network. You can see how by choosing this option for a new Bridged network. Then you can choose the group of interfaces you want to associate to this interface.
This will create a new virtual interface bridge which will have its own configuration as well as a real interface. So, despite the traffic goes through the bridge transparently, you can use the interface to offer other services like Zentyal administration UI or FTP.
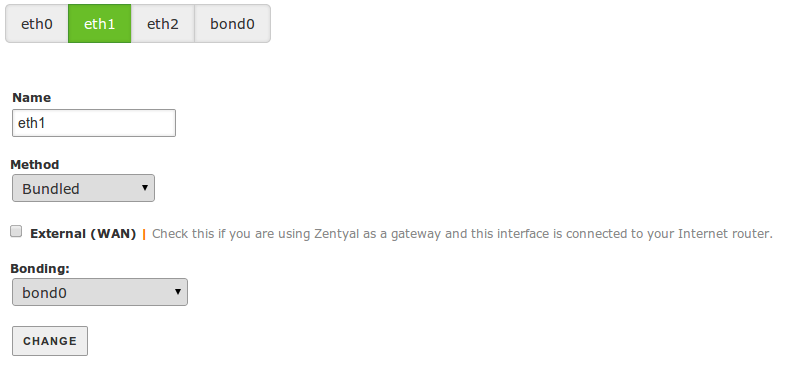
Bonding¶
You may want to bundle two or more physical network interfaces in order to create a virtual network interface with the sum of the network bandwidth.
The configuration is similar to the network bridge, you create the virtual interface bond<N> by configuring the first interface as Bundled and then, you will be able to add other network interfaces to this virtual device.
Bonding needs to be done on internal interfaces.
There are several Bonding modes available:
- Static: Send packets in parallel, in sequential order via each of the physical interfaces.
- LACP: Advanced control and negotiation protocol of phyiscal links. Need both ends supporting this standard.
- Balance (alb): Traffic balance based in negotiaing network capacity using ARP.
- Balance (tlb): Traffic balance based in current load and proportional capacity of each link.
- Backup: Enable additional links only if main one fails.
- Broadcast: Transmit all packets through all physical links. Protects against transmission errors but does not increase bandwidth.
Gateways and network Proxys¶
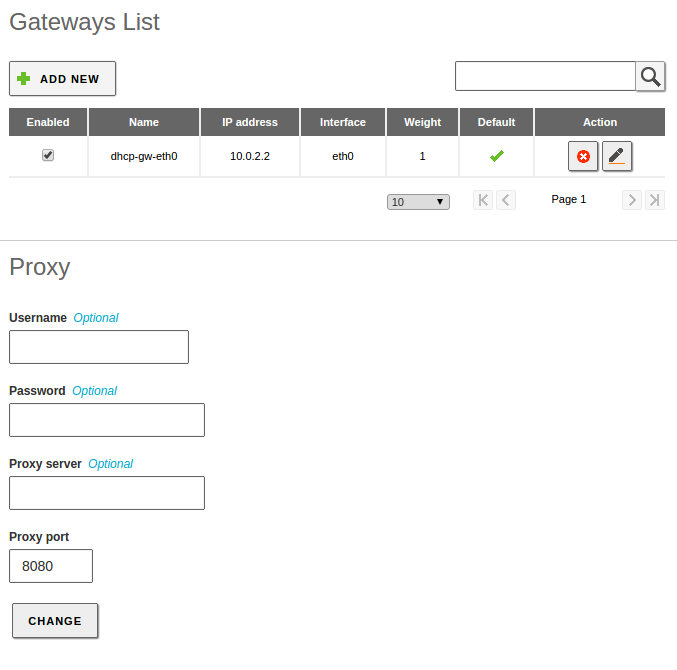
In case you need to configure the network interface manually, define the gateway to Internet using . Normally this is automatic if DHCP or PPPoE is in use, but not in other cases. For each gateway you can indicate the Name, IP address, Interface to which it is connected. The Weight defines the priority compared with other gateways and whether it is Predetermined by all of them.
In addition, if an HTTP proxy is required for Internet access, you can also configure this in this section. This proxy will be used by Zentyal for connections, such as updates and the installation of packages or the update of the anti-virus data files.
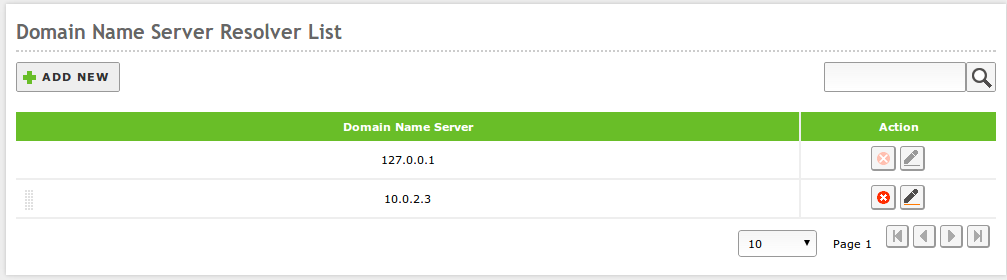
DNS¶
To allow the system to resolve domain names, you must indicate the address of one or several name servers in .
Network diagnosis¶
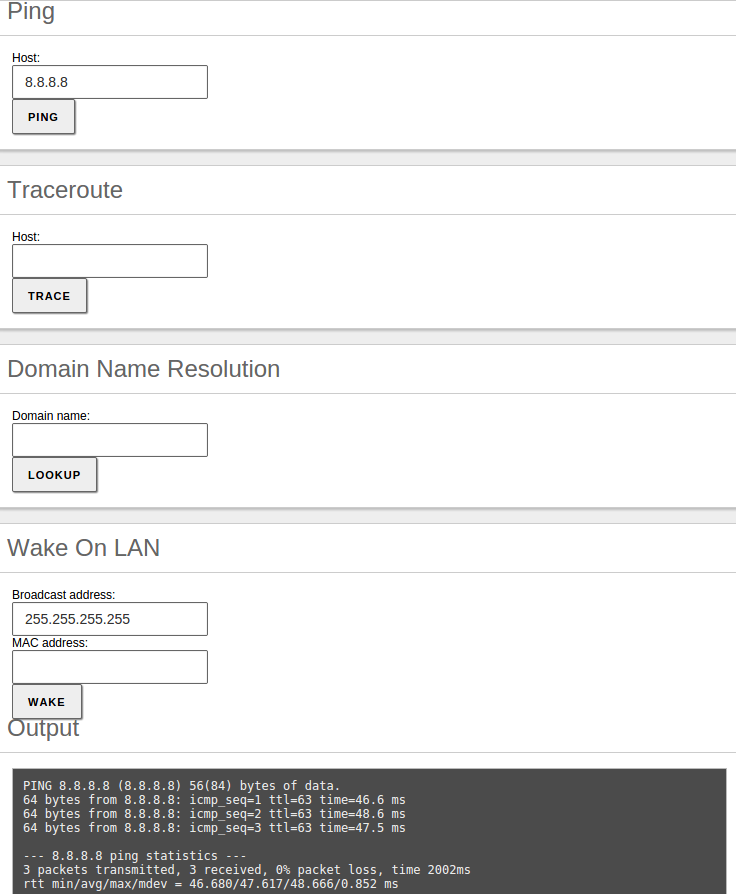
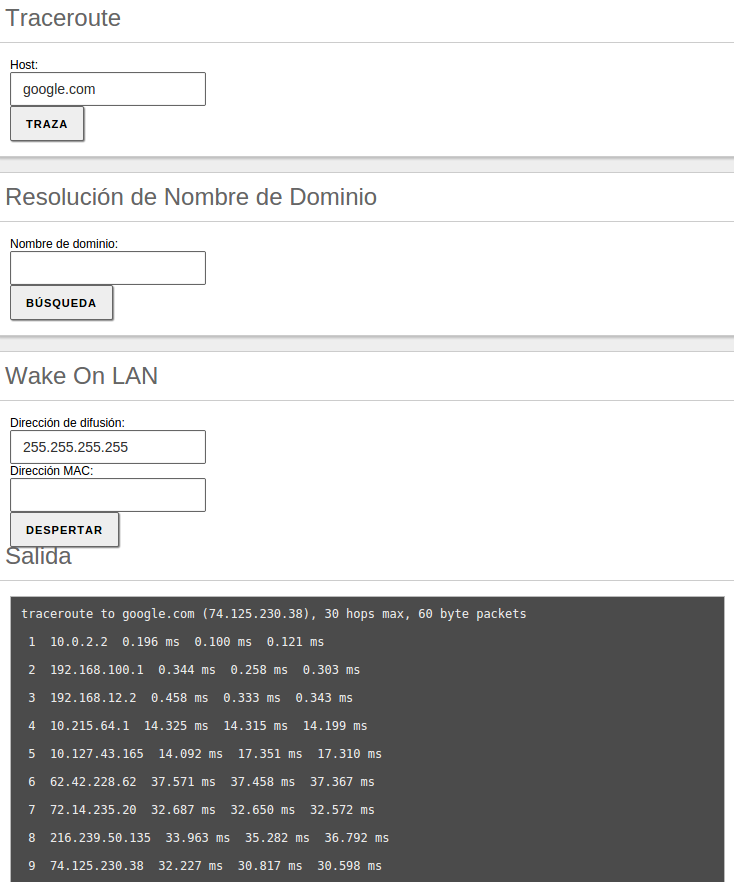
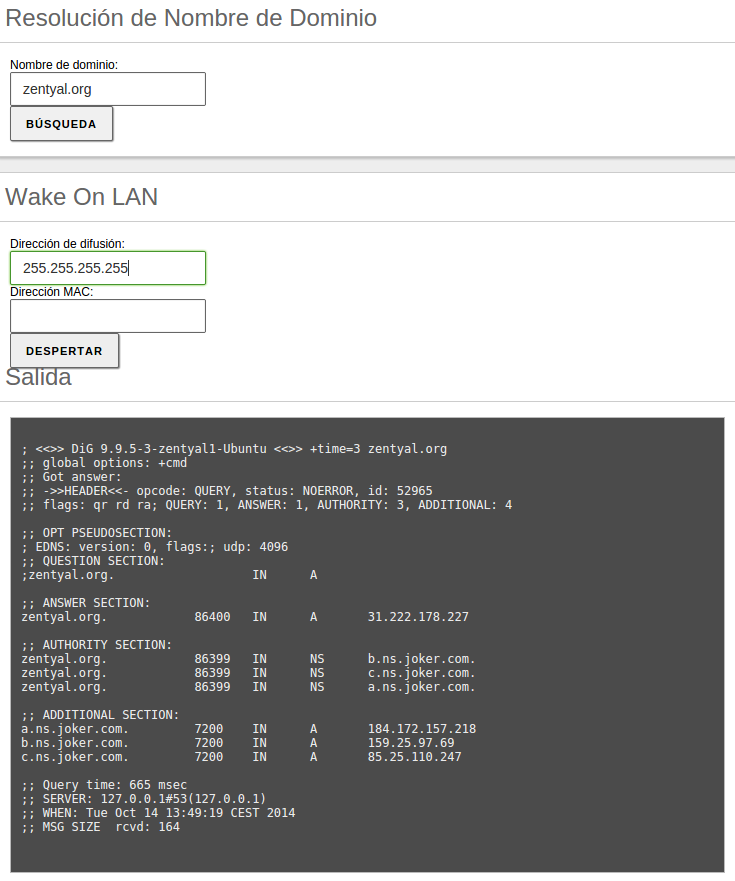
To check that the network has been configured correctly, you can use the tools available in .
Ping is a tool that uses the ICMP network diagnosis protocol to observe whether a particular remote host is reachable by means of a simple “echo request”.
You can also use the traceroute tool that is used to determine the route taken by packages across different networks until they reach a given remote host.
Also, you can use the domain name resolution tool, which is used to verify the correct functioning of the name service.
The last tool is Wake On Lan, which allows you to activate a host using its MAC address, if this feature is enabled in the target.