Mail filter¶
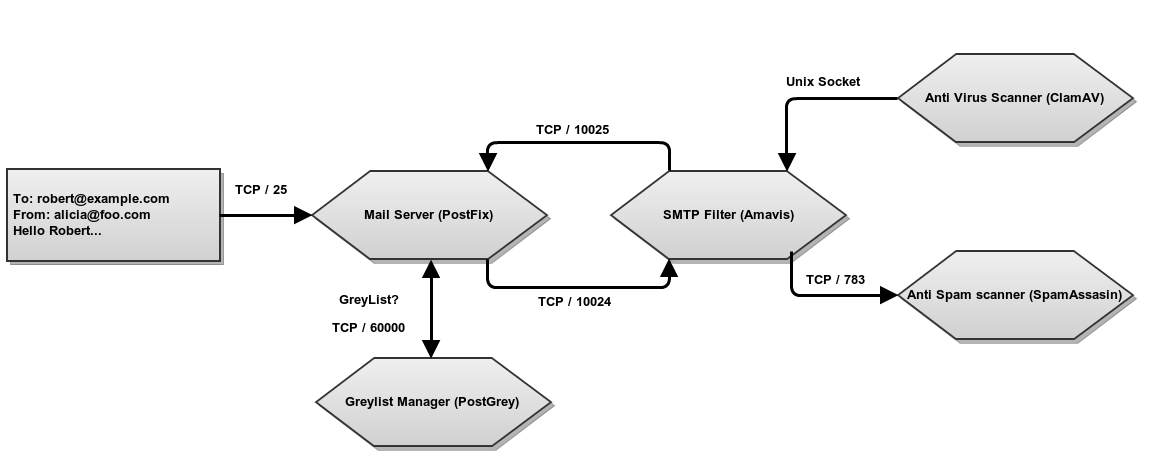
Mail filter schema in Zentyal¶
Zentyal offers a powerful and flexible mail filter to defend your network and users from these threats.
In the figure, you can see the different steps an e-mail passes through before being tagged as valid or not. First, the email server sends it to the greylisting policies manager and if considered as potential spam, the system requests that the email is forwarded to the source server. If the email passes through this filter, it will move to the mail filter. This will use a statistical filter to check a series of email features to discover whether it contains virus or is junk mail. If the email passes through all the filters, it is considered valid and it is sent to the recipient or stored on the server’s mailbox.
In this section the details of each filter and how to configure them in Zentyal will be explained step by step.
Grey list¶
The grey lists [1] exploit the expected performance of mail servers dedicated to spam. The behaviour is matched and all mail from the servers is discarded or not, hindering the spamming process.
These servers are optimised to send as many emails as possible in minimal time. For this, messages are auto-generated and sent without caring if they are received. When you have a grey list system, the emails considered as potential spam are rejected and the mail server is asked to send the email again. If the server is actually a spammer server, it probably doesn’t have the necessary tools to manage this request and therefore the email will never reach the recipient. On the contrary, if the email was legitimate, the sending server will simply re-send mail.
| [1] | Zentyal uses postgrey (http://postgrey.schweikert.ch/) as a postfix policy manager. |
The Zentyal strategy is to pretend to be out of service. When a new server sends an email, Zentyal responds “I am temporarily out of service” during the first 300 seconds [2]. If the sending server complies with the request, it will re-send the email after this time and Zentyal will mark it as a valid server.
Zentyal does not include email sent from internal networks on the gray list, or from objects with an allowed email relay policy or from addresses that are in the antispam whitelist.
| [2] | Actually the mail server responds “Greylisted”, i.e. moved to the grey list and pending to allow or disallow the mailing once the configured time has passed. |
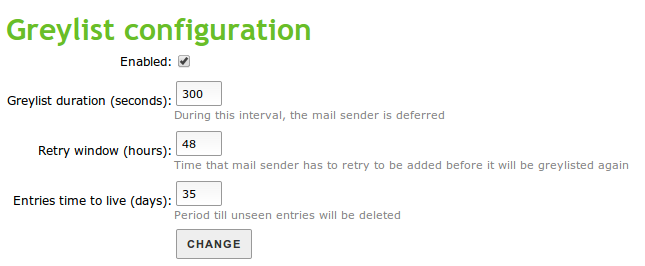
The Grey list can be configured via Mail ‣ Grey list with the following values:
- Enabled:
- Click to enable greylisting.
- Grey list duration (seconds):
- Seconds the sending server must wait before re-sending the email.
- Retry window (hours):
- Time in hours in which the sending server can send mail. If the server receives any mail during this time, this server will go to the grey list. In a grey list the server can send all the emails it wishes with no time restrictions.
- Entry time-to-live (days):
- Days the data of the evaluated servers will be stored in the grey list. After the configured days, when the server sends email again, it must go through the greylisting process described above.
Content filtering system¶
The mail content filtering is processed by the antivirus and spam detectors. To carry out this task, Zentyal uses an interface between the MTA and these applications. Therefore, the amavisd-new [3] application is used to ensure that the email is not spam and it does not contain viruses.
In addition, amavisd carries out the following checks:
- File extension and black and white lists.
- Mail filtering of emails with malformed headers.
| [3] | Amavisd-new: http://www.ijs.si/software/amavisd/ |
Antivirus¶
Zentyal uses the ClamAV [4] antivirus, an antivirus toolkit especially designed to scan email attachments in a MTA. ClamAV uses a database updater that allows the programmed updates and digital signatures to be updated via the freshclam program. Furthermore, the antivirus is capable of native scanning of a number of file formats, such as Zip, BinHex, PDF and so on.
| [4] | Clam Antivirus: http://www.clamav.net/ |
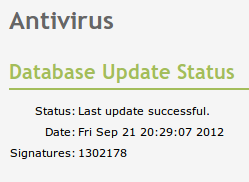
In Antivirus you can check if the system’s antivirus is installed and updated.
You can update it from Software Management, as you will see in Software updates.
It is optional to install the antivirus module, but if you do install it, you can see that it integrates several other Zentyal modules. This integration increases the security of the configuration options of different services, such as the SMTP filter, HTTP proxy or file sharing.
Antispam¶
The antispam filter gives each email a spam score and if the email reaches the spam threshold it is considered junk mail. If not, it is considered as legitimate email. The latter kind of email is often called ham.
The spam scanner uses the following techniques to assign scores:
- Blacklists published via DNS (DNSBL).
- URI blacklists that trac antispam websites.
- Filters based on the message checksum, checking emails that are identical, but with some few changes.
- Bayesian filter, a statistical algorithm that learns from its past mistakes when classifying an email as spam or ham.
- Static rules.
- Other. [5]
Zentyal uses Spamassassin [6] as spam detector.
| [5] | You can find a long list of antispam techniques at http://en.wikipedia.org/wiki/Anti-spam_techniques_(e-mail) |
| [6] | The Powerful #1 Open-Source Spam Filter http://spamassassin.apache.org . |
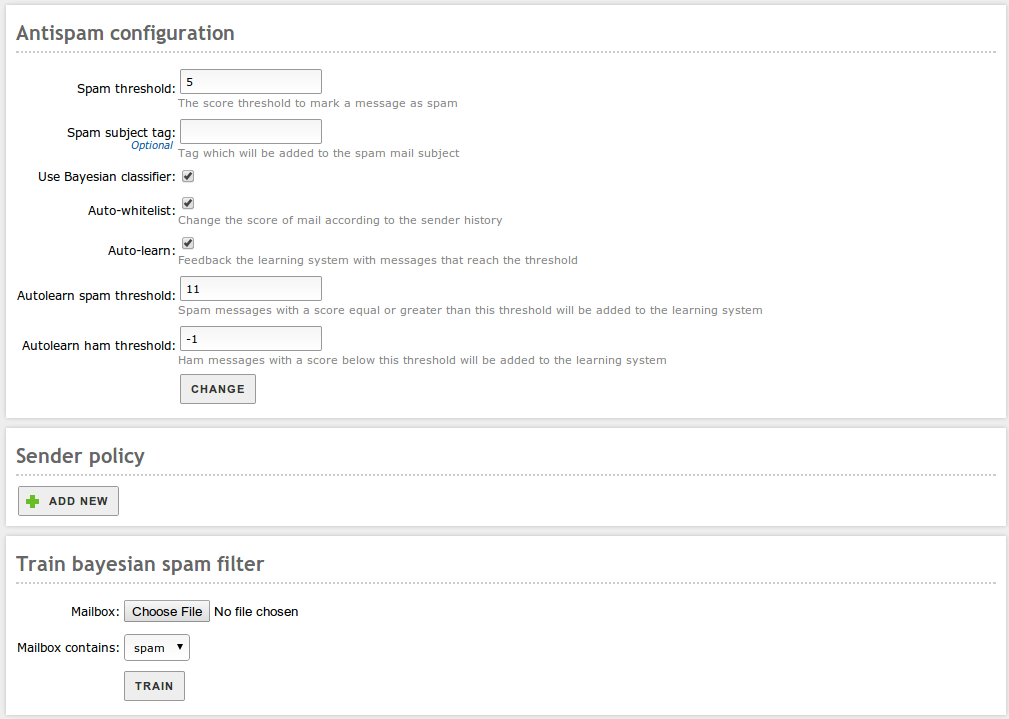
The general configuration of the filter is done from Mail filter ‣ Antispam:
- Spam threshold:
- Mail will be considered spam if the score is above this value.
- Spam subject tag:
- Tag to add to the mail subject in case it is spam.
- Use Bayesian classifier:
- If marked, Bayesian filter will be used. Otherwise it will be ignored
- Auto-whitelist:
- Considers the account history of the sending server when giving the score to the message; if the sender has sent plenty of ham emails, it is highly probable that the next email will be ham and not spam.
- Auto-learn:
- If marked, the filter will learn from the received messages, which score passes the auto-learn thresholds.
- Autolearn spam threshold:
- The filter will learn that email is spam if the score is above this value. You should not set a low value, since it may cause false positives. The value must be greater than the spam threshold.
- Autolearn ham threshold:
- Filter will learn if the email is ham if the score is below this value. You should not set a high value, since it may cause false negatives. The value must be less than 0.
From Sender Policy you can configure senders whose emails are always accepted (whitelist), always marked as spam (blacklist) or always processed by the antispam filter (process). If a sender is not listed here, the default behaviour will be process.
From Train Bayesian spam filter you can train the Bayesian filter by sending it a mailbox in Mbox [7] format, containing only spam or ham. You can find many sample files from the Internet to train the Bayesian filter, but usually you get more accurate results if you use email received from the sites you need to protect. The more trained the filter is, the better results you get when testing if a message is junk or not.
| [7] | Mbox and maildir are email storage formats, independent of the the used email client. For Mbox, all the emails are stored in a single file, whilst maildir organises emails into separate files within a directory. |
SMTP mail filter¶
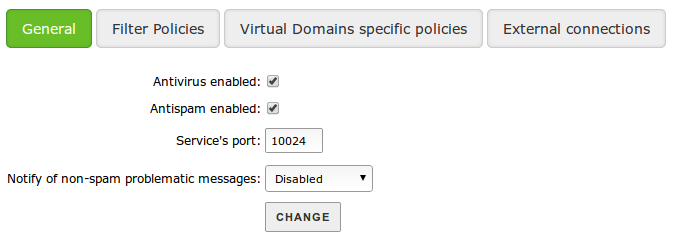
From Mail filter ‣ SMTP mail filter you can configure the behaviour of the described filters, when Zentyal receives mail by SMTP. From General you can configure the general behaviour of all incoming mail:
- Enabled:
- Check to enable SMTP filter.
- Antivirus enabled:
- Check to ensure the filter searches for viruses.
- Antispam enabled:
- Check to ensure the filter searches for spam.
- Service’s port:
- Port to be used by the SMTP filter.
- Notify of non-spam problematic messages:
- You can send notifications to a mailbox when you receive problematic emails that aren’t spam, for example, emails infected by a virus.
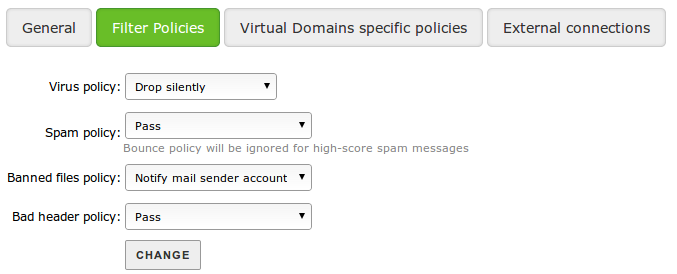
From Filter policies you can configure how the filter must act with different types of emails.
You can perform following actions with problematic emails:
- Pass:
- Do nothing, let the email reach its recipient. Nevertheless, in some cases like viruses, the mail server will add a warning to the email subject.
- Notify mail server account:
- Discard the message before it reaches the recipient, notifying the original sender account.
- Notify sender server:
- Discard the message before it reaches the recipient, notifying the server of the sender account, it’s very common that, the server notifies its user in turn about this with a Undelivered Mail Returned to Sender message.
- Drop silently
- Discard the message before it reaches the recipient, without notifying the sender or his/her server.
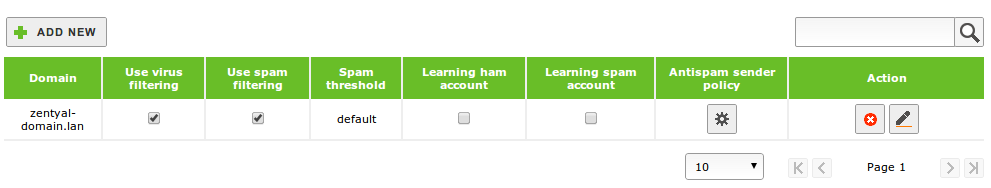
From Virtual domains you can configure the behaviour of the filter for virtual domains of the email server. These settings override the previously defined default settings.
To customise the configuration of a virtual domain of the email, click on Add new.
The parameters that can be overridden are the following:
- Domain:
- Virtual domain you want to customise. Those configured in Mail ‣ Virtual domain are available.
- Use virus / spam filtering:
- If enabled, the email received in this domain will be filtered in search of viruses or spam
- Spam threshold:
- You can use the default score for spam or custom value.
- Ham / spam learning account:
- If enabled, ham@domain and spam@domain accounts will be created. The users can send emails to these accounts and train the filter. All the email sent to ham@domain will be recorded as not spam the email sent to spam@domain will be recorded as spam.
Once you have added the domain, you can add addresses to your whitelist, blacklist or force the processing from Antispam policy for senders.