Virtual Private Network (VPN) Service with IPsec¶
Zentyal integrates OpenSwan [2] as its IPsec solution. This service uses the ports 500 and 4500 of UDP and the ESP protocol.
| [2] | http://www.openswan.org/ |
Configuring an IPsec tunnel in Zentyal¶
To configure IPsec in Zentyal go to VPN ‣ IPsec. Here you can define all the tunnels and IPsec connections you need. You can enable or disable each one of them and add an explanatory text.
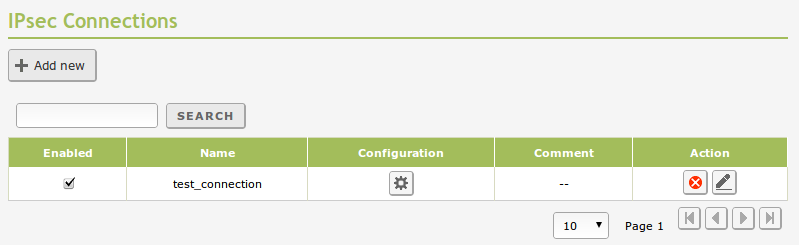
IPsec connections
Inside Configuration, and the General tab you will define the Zentyal’s IP address that you will use in each connection to access the external subnet, the local subnet behind Zentyal that will be accessible through the VPN tunnel, the remote IP address you will contact in the other end of the tunnel and the local subnetwork you will have available in the other end. If you want to configure a tunnel between two networks using IPsec, both ends must have a static IP address.
Currently Zentyal supports PSK authentication only (preshared key), which you can configure under PSK preshared key.
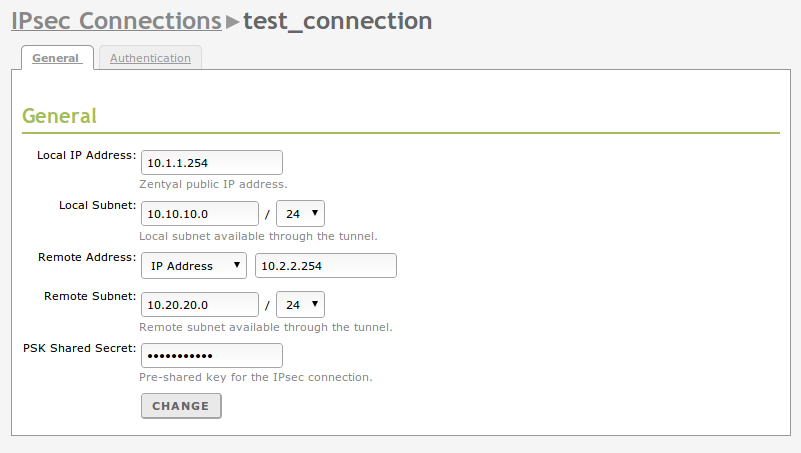
General configuration
In the Authentication tab you will configure the specific parameters of the tunnel authentication. This parameters determine the behaviour of the IPsec protocol and have to be identical in both ends of the tunnel. To learn more about the meaning of each one of the options, check IPsec specific documentation.
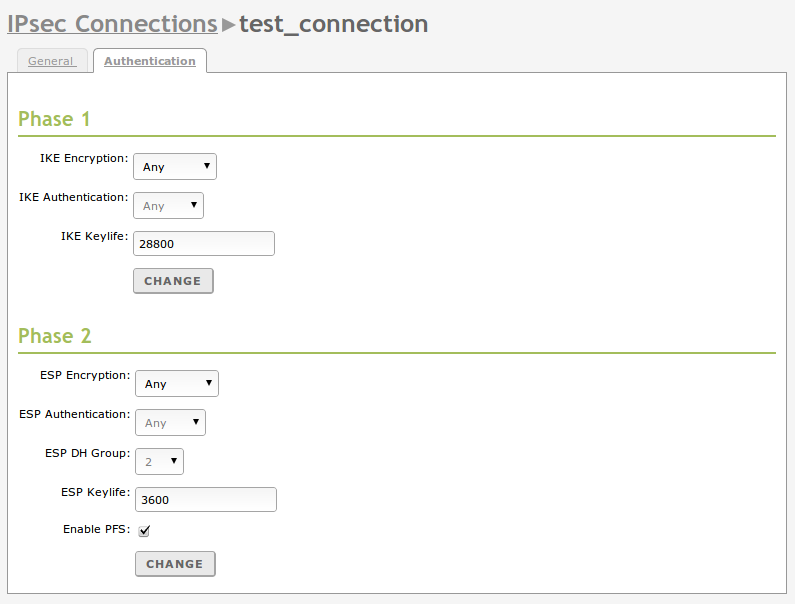
Authentication configuration